Smart Cities Face a Dynamic Cybersecurity Landscape

Who will you meet?
Cities are innovating, companies are pivoting, and start-ups are growing. Like you, every urban practitioner has a remarkable story of insight and challenge from the past year.
Meet these peers and discuss the future of cities in the new Meeting of the Minds Executive Cohort Program. Replace boring virtual summits with facilitated, online, small-group discussions where you can make real connections with extraordinary, like-minded people.
In yesterday’s blog post I put forward an idea: tech-powered urban innovations will not only make cities more efficient, they’ll help to transform how those cities operate, how they connect with (and listen to) citizens and visitors, and that may portend even bigger changes on the near-horizon.
The range of functions that a smart city can integrate digitally is growing exponentially. It typically includes connected and remotely accessible city assets or public spaces in which connectivity allows new patterns and styles of public engagement and municipal service delivery. But a smart city also introduces tremendous value through more mundane, but equally important, functions like parking, lighting, security, Wi-Fi and energy management. As IoT grows, cities (or even regions) can more affordably invest in and increasingly benefit by sharing their capabilities.
Decisions involving technology are a daily function of city life, impacting all of the ways that we live, work, play, and learn. With increasing investments in infrastructure — especially for more advanced data networks and communications networks — cities find themselves on a path to full connectivity. From publicly-accessible websites to back-end administration of complex city services (like street lights and parking), today’s cities could not exist without using a host of new digital tools. In a very short time, such technology has become critical to their success – and survival.
Those who own or operate a city’s most vital assets – urban transport systems, urban water systems, urban energy systems, urban building systems – are hoping that someone will soon deliver intelligent cybersecurity relevant to the real world of cities. That means using comprehensive advanced threat protection – which, in turn, means gaining access to a portfolio of solutions and services that are integrated, pervasive, continuous and open.
A threat-centric approach to security is needed because it reduces complexity, while providing unmatched visibility, continuous control and advanced threat protection across the entire attack continuum, allowing cities (and especially those responsible for key city assets) to act smarter and more quickly — before, during, and after an attack.
Perhaps the core security challenge facing us all today is the changing threat landscape. Agile ‘bad actors’ are increasingly better funded, and during the past few years they’ve steadily been improving their approaches – resulting in much more effective attacks. Just 10 years ago cyber-security professionals active in this field were focused on less sophisticated attacks, like Blaster and Slammer. We were getting phishing emails from guys in Nigeria saying “if you give me $10 today, I’ll give you $1000 in 2 weeks.” And they were poorly worded so we could spot them easily. But today, think about how much more sophisticated the attackers are. They are going on to LinkedIn, studying very detailed information about your companies and your employees and then sending targeted emails to people to click on a malicious link. What the best companies have done in response is to add many new security solutions to stop these problems, but we’re now stuck dealing with complexity.
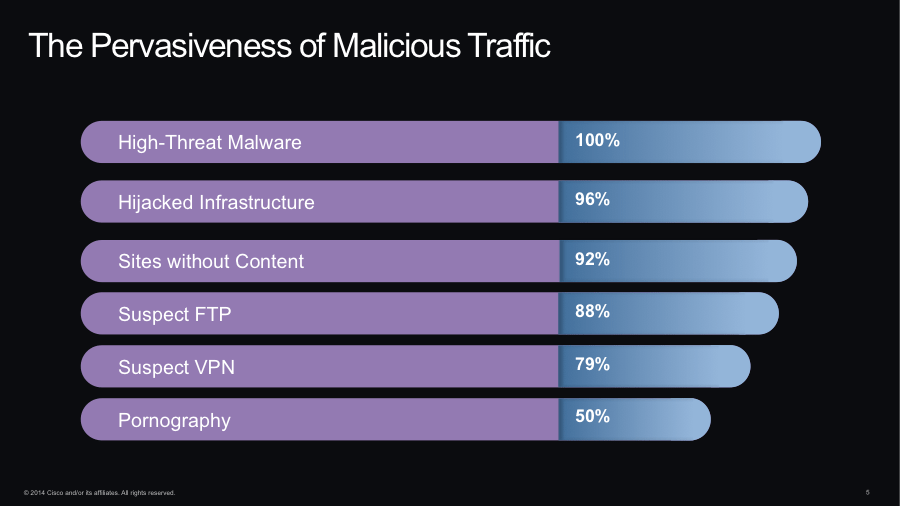
Malicious traffic is visible on 100 percent of corporate networks and on 100 percent of government networks. There is abundant evidence that sophisticated criminals or other players have penetrated these networks and may be operating undetected over long periods of time.
In one recent review of DNS lookups originating from inside corporate networks, threat intelligence experts found that in every case, organizations showed evidence that their networks had been misused or compromised. For example, 100 percent of the business networks analyzed by Cisco had traffic going to websites that host malware, while 92 percent show traffic to webpages without content, which typically host malicious activity. 96 percent of the networks reviewed showed traffic to hijacked servers.
Technology changes at a rapid pace – with new innovations available in all key categories, such as cloud, mobility, explosion in applications, Big Data and IoT. Each of these advances, and the changing business models, create new attack vectors, and these are being exploited by hackers.
The combination of cloud computing and mobility is a perfect storm of security threats, and you should prepare for these threats as if there’s a storm coming. As citizens and governments and businesses all become increasingly mobile, so does sensitive data. In fact, in a recent survey conducted by ESG, many of the best cybersecurity professionals concluded that there are some big risks associated with the mobility enabled by cloud infrastructure services, and on the top of their list of risks are these: a lack of control, privacy, visibility plus inapplicability of uniform policy.
How did we get to this point of increased over-complexity? If you think about the way security has evolved, it all began within the perimeter. If you are inside the perimeter, you are trusted; if you are outside, you are untrusted. That worked for a long time, but it’s clearly not working today because many people are outside the network. They are on any device, accessing any application and in many different clouds. That information is being accessed through the data center, though public clouds, and though hybrid clouds (which combine elements of both the public and private). This is creating what some now call the ‘Any-to-Any problem’: any user on any device, anywhere, is accessing any application at any time. And one look at the trend-line tells us that it’s only going to get more challenging.
A few relevant data points are worth mentioning here:
- 300% growth of malicious samples, as analyzed year over year.
- Many thousands of new cloud-delivered applications are being offered every month.
- In almost every one of the Fortune 500’s business networks, as analyzed over the course of the year, 100% had traffic going to websites that host malware. This means that these networks have been hacked and/or legitimate users have been tricked into clicking on fraudulent web pages.
- Cisco’s ‘Annual Security Report’ indicates that overall vulnerability and threat alerts have reached their highest levels since Cisco began tracking them in 2000.
While the specific industry vertical targeted by attackers often fluctuates, businesses in the core urban industries (water systems, power systems, transport systems, building systems) now appear to be getting much more attention from cybercriminal groups. Some analyses are finding significant growth in key industries, and cybercriminals may be seizing on newly emerging vulnerabilities resulting from the Internet of Things revolution that’s connecting disparate and discrete objects and end-points to networks. Indeed, the Denial of Service attack of October 21, 2016 – which targeted critical infrastructure and Dyn Corp – was enabled by security weaknesses built into consumer devices which are capable of Internet of Things connectivity, such as baby crib monitors.
Security problems that cities face today are manifold. With sophisticated threats and an any-to-any infrastructure, cities and those who serve cities are seeing three big challenges and areas of uncertainty:
-
Changing business models and attack vectors
- How to maintain security posture and compliance as the IT landscape – mobility, cloud, the Internet of everything – is fast-changing?
-
A dynamic threat landscape
- How to improve our ability to continuously protect against new attack vectors and the increasing sophistication of threats?
-
Complexity and fragmentation of security solutions
- How to work on the first two problems while at the same time reducing complexity in our environments?
The combination of these dynamics has created security gaps, broken the security lifecycle and reduced visibility – and is creating increased complexity and management challenges.
There is no such thing as a silver bullet in security. Many still gravitate to the hope that there will someday be a magical solution to solve all of our cyber issues. The current suite of solutions is a set of disparate point products that solve one problem, but provide gaps for the bad guys to exploit. Add to this one other problem: the separation of technologies on the network from those on endpoints, mobile devices, and virtual environments, and you create some of the gaping holes that bad actors use to accomplish their dark missions.
Malware is everywhere and it’s incredibly challenging to combat, using whatever unprotected path exists to reach its target and accomplish its mission. Malware has become the weapon of choice for hackers. According to the Verizon Data Breach Investigation Report, of the top 20 types of threat actions, malware is the most common method used, followed by hacking and social engineering. Increasingly, blended threats that combine several methods – for example, phishing, malware and hacking – are being used to introduce malware, embed the malware in networks, remain undetected for long periods of time and steal data or disrupt critical systems.
With regard to these blended threats, the report tells us that more than 95 percent of all attacks intended to conduct espionage employed phishing. A prominent recent retail breach began with a targeted email phishing attack ultimately led to the access of payment system data via malware uploaded to Point of Sale systems. Websites hosted on compromised servers are now acting as both a redirector (the intermediary in the infection chain) and a malware repository. Other attack examples include:
- ‘Watering hole’ attacks targeting specific industry-related websites to deliver malware
- Malware delivered to users legitimately browsing mainstream websites
- Spam emails that appear to be sent by well-known companies but contain links to malicious sites
- Third-party mobile applications laced with malware and downloaded from popular online marketplaces.
I am sure many of you can sympathize with this problem of complexity. There are multiple managers and identity stores, isolated threat intelligence, inconsistent enforcement and too many vendors.
Security has to be agile, and it has to be continuous. We also have a lot of complexity as we begin to combine all of this information, applications, and sensitive information, which creates a point of focus and can be a point of attack for the bad guys.
As cities enable their employees and citizens to access applications through multiple channels they have to secure such access. Increasingly, their priority is to protect the end-users and the systems themselves. This means that cities have to provide the right levels of access, inspection and protection against adversaries — because the massive complexity of anyone connecting from any device is forcing big adjustments to be made. Where to start with shoring up the security of such systems? Where to enforce the new rules?
Concluding thoughts to consider:
- It’s very hard to have security implemented when everything can connect to everything.
- It’s easy for attackers to hack into systems when they can gain access via multiple points of entry — and we’re already seeing that.
- New attacks are being focused directly on mobile devices that are connected to the city networks.
- Complexity increases as all of this information, multiple applications, and sensitive information are combined; this has become a point of attack and point of focus for the bad guys.
- Cities and their partners (like utilities) have to provide the right levels of access, inspection and protection against our adversaries.
A smart city’s connectedness is about much more than just the city’s operational networking, and much more than its transactional networking. A variety of disparate connections are being built, such as sensor-based smart parking and street lighting. The aim is to create a more accessible, safer and energy efficient city. True connectedness includes social and visual technologies that reshape spaces for public interaction. The smartest cities are the ones actively encouraging more nuanced relationships between and amongst everyone inside the city. It’s a lofty goal, but the good news is that it’s doable.
Discussion
Leave your comment below, or reply to others.
Please note that this comment section is for thoughtful, on-topic discussions. Admin approval is required for all comments. Your comment may be edited if it contains grammatical errors. Low effort, self-promotional, or impolite comments will be deleted.
1 Comment
Submit a Comment
Read more from MeetingoftheMinds.org
Spotlighting innovations in urban sustainability and connected technology
Middle-Mile Networks: The Middleman of Internet Connectivity
The development of public, open-access middle mile infrastructure can expand internet networks closer to unserved and underserved communities while offering equal opportunity for ISPs to link cost effectively to last mile infrastructure. This strategy would connect more Americans to high-speed internet while also driving down prices by increasing competition among local ISPs.
In addition to potentially helping narrow the digital divide, middle mile infrastructure would also provide backup options for networks if one connection pathway fails, and it would help support regional economic development by connecting businesses.
Wildfire Risk Reduction: Connecting the Dots
One of the most visceral manifestations of the combined problems of urbanization and climate change are the enormous wildfires that engulf areas of the American West. Fire behavior itself is now changing. Over 120 years of well-intentioned fire suppression have created huge reserves of fuel which, when combined with warmer temperatures and drought-dried landscapes, create unstoppable fires that spread with extreme speed, jump fire-breaks, level entire towns, take lives and destroy hundreds of thousands of acres, even in landscapes that are conditioned to employ fire as part of their reproductive cycle.
ARISE-US recently held a very successful symposium, “Wildfire Risk Reduction – Connecting the Dots” for wildfire stakeholders – insurers, US Forest Service, engineers, fire awareness NGOs and others – to discuss the issues and their possible solutions. This article sets out some of the major points to emerge.
Innovating Our Way Out of Crisis
Whether deep freezes in Texas, wildfires in California, hurricanes along the Gulf Coast, or any other calamity, our innovations today will build the reliable, resilient, equitable, and prosperous grid tomorrow. Innovation, in short, combines the dream of what’s possible with the pragmatism of what’s practical. That’s the big-idea, hard-reality approach that helped transform Texas into the world’s energy powerhouse — from oil and gas to zero-emissions wind, sun, and, soon, geothermal.
It’s time to make the production and consumption of energy faster, smarter, cleaner, more resilient, and more efficient. Business leaders, political leaders, the energy sector, and savvy citizens have the power to put investment and practices in place that support a robust energy innovation ecosystem. So, saddle up.






Niger State Government, Nigeria, is preparing a Plan for a SMART New Town near Abuja, federal capital territory of Nigeria. Do you think the benefits of such a project outweighs the risk of hacking and hackers?- for a developing country like Nigeria with its weak capacity to manage its cities.
Kindly advise